¿Podés explicar hoy tu postura de ciberseguridad sin improvisar?
Si un cliente, auditor o aseguradora te pide claridad y evidencias, lo que te expone no es la falta de herramientas: es la falta de ownership y prioridades ejecutivas.
Sesión 1:1 de 30 minutos. Revisamos tu nivel real, 3 riesgos críticos y definimos el punto de partida más razonable (GAP 60 días / Implementación / Programa integral).
El problema no es la ciberseguridad. Es la improvisación bajo presión
-
Tenés herramientas, pero no una historia clara para explicarlas a terceros.
-
Nadie puede decir con seguridad “esto alcanza / esto no alcanza”.
-
El roadmap cambia según urgencias, no según riesgo.
-
Cuando aparece un cuestionario, auditoría o incidente, la dirección queda expuesta.
Si hoy esa conversación sería incómoda, este programa existe para ordenarla en serio.
¿Es para tu empresa?
Este framework está diseñado para:
-
Startups y PYMEs de 5 a 500 empleados que manejan datos sensibles de clientes, pagos o información crítica.
-
Empresas que reciben cuestionarios de seguridad, auditorías o requisitos de clientes corporativos o partners internacionales.
-
Equipos que ya tienen herramientas (firewall, antivirus, backup, cloud, etc.) pero sin un marco claro, sin prioridades y sin evidencias ordenadas.
-
Directores, CEOs, CTOs o responsables de IT que quieren hablar de seguridad en lenguaje de negocio, no solo en términos técnicos.
-
Organizaciones que necesitan resultados visibles en 60 días, no proyectos eternos.
-
Empresas que ya sienten fricción en ventas enterprise por cuestionarios / evidencias.
-
Líderes que saben que hoy no podrían explicar su postura de seguridad en 5 minutos sin “armar algo”.
Si te ves en esta lista, el Programa Talsoft de Madurez es el atajo para ordenar tu seguridad sin convertirte en una gran corporación.
Qué vas a lograr
-
Claridad ejecutiva (sin improvisar) de dónde estás parado.
-
Prioridades con dueño y fechas.
-
Evidencias defendibles (clientes/auditorías/seguros)
Señales de exposición ejecutiva (2 minutos)
Esto no es un diagnóstico ni una recomendación.
Es un chequeo rápido para detectar si hoy hay señales de improvisación bajo presión externa
(clientes, auditorías, aseguradoras) y brechas sin dueño claro.
1) Si mañana un cliente/auditor pide tu postura de seguridad, ¿podés responder sin improvisar?
2) ¿Hay un responsable claro de decidir prioridades de seguridad (no solo ejecutar tareas)?
3) En los próximos 6–12 meses, ¿esperás presión externa por seguridad?
Cómo trabajamos con tu empresa
Pasos
1- Diagnóstico de Madurez (0–60 días)
Relevamos tu situación actual, riesgos clave, controles existentes y brechas.
2- Roadmap y Quick Wins (30–90 días)
Definimos entre 8 y 12 controles críticos para tu contexto (técnicos, procesos y evidencias).
3- Acompañamiento y Evidencias (dos opciones)
Te ayudamos a implementar, medir y documentar para clientes, auditoras, aseguradoras o inversores.
Opciones:
-
Acompañamiento para implementar (Full)
-
Programa integral con continuidad (VIP)
Sin paquetes ocultos, sin letra chica: un método claro, aplicable y probado en empresas reales de LATAM y mercados internacionales.
Por qué no conviene esperar 6 meses
Postergar la ciberseguridad hoy tiene impacto directo en el negocio:
-
Esperar no reduce el riesgo: solo te deja sin respuesta cuando te lo exigen.
-
Los ataques a PYMEs y startups (phishing, ransomware, robo de accesos) aumentan y apuntan a entornos con controles básicos mal implementados.
-
Cada vez más clientes, partners y aseguradoras piden políticas, controles y evidencias formales antes de firmar contratos.
-
Muchas pólizas de ciberseguro pueden rechazar o limitar coberturas si no tenés controles mínimos documentados y verificados.
-
Resolver después de un incidente siempre es más caro, más lento y más desgastante para la dirección.
Por eso ofrecemos un número limitado de diagnósticos gratuitos por mes, para dedicar tiempo real al análisis de cada empresa.
Este framework se implementa empezando SIEMPRE por el Paquete Inicial GAP
En escenarios sin recursos internos, el GAP es el inicio, pero se diseña desde el día 1 para ejecución (Full) y continuidad (VIP)
Paquete Inicial GAP – Diagnóstico en 60 días
Punto de entrada recomendado al Programa Talsoft de Madurez.
Para empresas que necesitan una foto clara, rápida y accionable de su ciberseguridad.
En este paquete:
– Evaluamos tu situación según los 6 niveles de madurez.
– Identificamos riesgos críticos y brechas prioritarias.
– Armamos un roadmap 30–60–90 días con responsables y hitos.
– Presentamos los resultados en sesiones ejecutivas, en lenguaje de negocio.
Resultado esperado:
Sabés exactamente dónde estás, qué hacer primero y cómo explicarlo a clientes, socios, aseguradoras y dirección.
Tu hoja de ruta: 6 niveles de madurez en ciberseguridad
En lugar de recetas genéricas, usamos un modelo de 6 niveles que traduce la ciberseguridad a un lenguaje que dirección, IT y negocio pueden entender.
Esto te permite saber con precisión:
-
Dónde estás hoy.
-
Qué deberías implementar primero.
-
Cómo justificar inversiones con criterios claros.
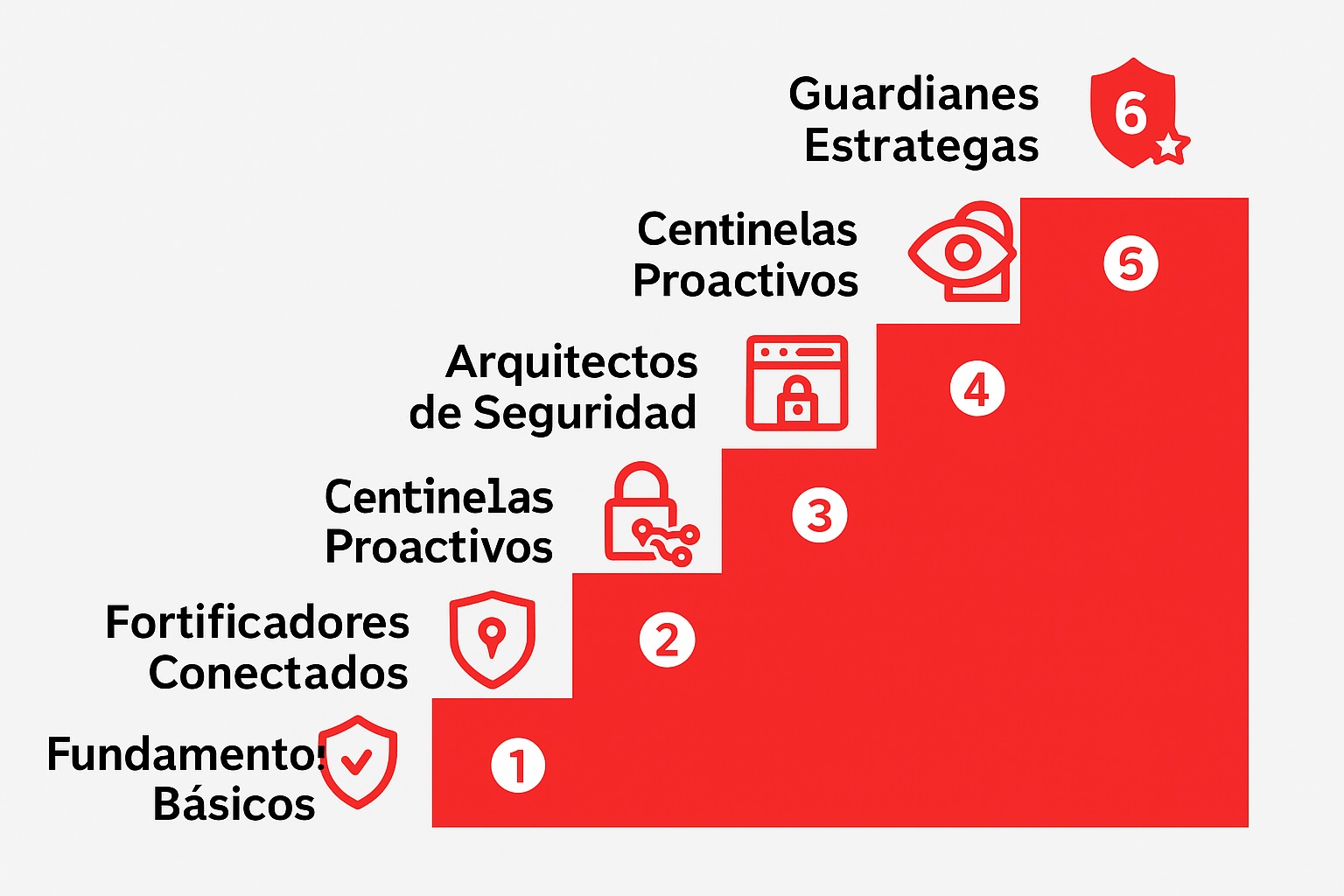
Nuestro Framework de Madurez en Ciberseguridad guía a tu empresa en un camino de 6 niveles progresivos, y es la base del Programa Talsoft de Madurez.
Con esta metodología ya estamos ayudando a empresas de la región a:
– Reducir incidentes y exposición de forma medible en 6–12 meses (según contexto y ejecución).
– Implementar controles alineados a CIS v8 e ISO 27001.
– Convertir la seguridad en una ventaja competitiva real.
Cómo podemos implementar tu roadmap
Sugerimos comenzar por el Paquete Inicial GAP dentro del Programa Talsoft de Madurez. El Full GAP, las Extensiones y la Membresía VIP se definen después del diagnóstico, solo si tiene sentido para tu empresa.
Full GAP + Implementación – Del diagnóstico a los resultados
Etapa de ejecución del Programa Talsoft de Madurez para llevar el roadmap a resultados.
Para empresas que quieren ejecutar el plan con acompañamiento experto.
Incluye todo el Paquete GAP Inicial, más:
– Implementación guiada de los controles priorizados (3–6–12 meses).
– Ayuda en políticas, procesos, hardening, monitoreo y evidencias.
– Seguimiento mensual con tablero ejecutivo.
– Definimos ownership por control/proyecto (quién decide, quién ejecuta).
– Unificamos evidencia y narrativa para clientes/auditores (no solo ejecución técnica).
– Alineación con CIS v8, ISO 27001 y requisitos de pólizas cyber.
Resultado esperado:
Controles funcionando, menos incidentes, evidencias listas y una historia sólida frente a clientes e inversores.
Extensiones del Programa de Madurez: activá resultados rápidos sin cambiar tu plan
Cyber-Insurance Readiness
- Para qué: renovar o mejorar póliza y bajar prima demostrando controles.
-
Qué entregamos: checklist de aseguradora (MFA/EDR/backups probados/IR), remediaciones críticas 30-60 días, paquete de evidencias para broker, simulacro de siniestro.
-
Resultados: reducción de exposición, tiempos de respuesta, y fricción en renovación.
AI-Safe Adoption (NIST AI RMF)
-
Para qué: usar IA con inventario, pruebas y guardrails — listo para auditor/cliente.
-
Qué entregamos: inventario de casos, políticas y roles, pruebas , runbooks de incidentes de IA, evidencias.
-
Resultados: adopción segura de IA, menos riesgo operativo y reputacional.
Lo que ya logramos con empresas como la tuya
Muy agradecido, un servicio muy profesional y con resultados inmediatos en un tema muy delicado, como la seguridad informática.
“Estuvimos recibiendo ataques en nuestro sitio web, desde el momento que contactamos a Talsoft nos atendieron al instante y se involucraron en la solución del problema, lo que más me impresiono fue su disponibilidad y empeño en ayudarnos a resolver el problema.”
“Entregaron un servicio de calidad y se acomodaron a los tiempos de entrega del proyecto, siendo que eran bastante acotados.”
“Más allá de la detección de riesgos internos y externos a nuestra organización, la sugerencia de un plan de acción con temas concretos a trabajar y mejoras a implementar hace que la auditoría de seguridad sea útil y efectiva“
“Con vuestros servicios de consultoría logramos mejorar la seguridad informática de nuestros sistemas, permitiéndonos alcanzar un nivel de excelencia y así certificar PCI-DSS.“
“Rapidez, eficiencia y resultados“
Beneficios inmediatos de aplicar el framework
– Velocidad para responder a terceros
– Menos fricción en ventas enterprise
– Menos desgaste directivo en incidentes
¿Ya hiciste tu GAP? Sumate a la Membresía VIP
La Membresía VIP es el siguiente paso natural después de aplicar el Programa Talsoft de Madurez:
– Seguimiento mensual de tu roadmap.
– Rol de Fractional CISO para tu empresa.
– Revisión de incidentes, ajustes y nuevas exigencias de clientes/aseguradoras.
– Evidencias siempre listas para auditorías y renovaciones.
– La VIP existe para que el sistema no dependa de “héroes” internos.
¿Por dónde empiezo?
Empezamos siempre con una consultoría gratuita de 30 minutos para entender tu contexto, estimar tu nivel de madurez y definir si el Paquete GAP Inicial del Programa Talsoft de Madurez tiene sentido para tu empresa.
Mirá cómo trabajamos con PYMEs y Startups (eventos grabados)
Antes de sumarte al Programa Talsoft de Madurez podés ver cómo pensamos la ciberseguridad para PYMEs y Startups. En estos eventos en vivo mostramos casos reales, errores frecuentes y ejemplos del framework aplicado en empresas de LATAM.
Preguntas Frecuentes
¿Qué tamaño de empresa atendemos?
Startups y PyMEs (5–500 empleados) y equipos en crecimiento.
¿Qué obtenemos al finalizar el assessment inicial?
Al finalizar el GAP Inicial del Programa Talsoft de Madurez obtenés un mapa de riesgos, un roadmap priorizado 30–60–90 días y un tablero ejecutivo con métricas.
¿Qué herramientas usan?
Stack abierto (Wazuh XDR, Cloudflare, AWS/GCP, SAST/DAST). Nos integramos a tu stack actual.
¿Cómo se mide el éxito?
Reducción de superficie expuesta, tiempos de detección/respuesta, cierre de brechas y cumplimiento.
¿Cómo es la inversión?
Paquetes cerrados (Start/Growth) y retainers mensuales. Cotizamos por alcance y urgencia.
¿Y si todavía no usamos IA?
Empezamos con inventario y política mínima; te preparamos para escalar sin riesgos.
¿Qué pide típicamente mi aseguradora?
MFA/EDR/backup probado/IR + evidencias; te damos todo en un solo paquete.
¿Ofrecen una consultoría gratuita?
Sí: sesión de 30 minutos para un diagnóstico express de madurez y próximos pasos dentro del Programa Talsoft de Madurez.
